
Review of reverse engineering (i.e. software reversing) tools. Advantages and disadvantages, alternative solutions.
Reverse engineering or software reversing, is a set of techniques use to analyze closed source software in order to extract seemingly unavailable information, e.g. algorithms, hidden access passwords (e.g. to databases), information on how certain files are encrypted, and so on.
Reverse engineering is used for example in the fields of software analysis for potential security vulnerabilities (exploitation), malware analysis (antivirus developers) or software and games localization.
Advanced software analysis requires the knowledge of examined files structure, so most often a knowledge of executable files formats is required, Portable Executable for Windows system or ELF format for Linux type systems. It is also required to know basis of assembler for 32 and 64 bit platforms, in order to understand properly compiled code in closed-source software, its structure and widely used conceptions and software constructions transformed into binary data.
Even having appropriate knowledge, we will not be able to use it without proper tools. In this article, I'd like to present dedicated tools, used in reverse engineering, divided into categories. The majority of the dedicated tools, divided into categories presented here, qualify as a material for separate articles; however, it was my idea to present as many types of software as possible to show a variety of uses.
Complicated character of reverse engineering software and the process of its creation is often connected with the fact that those programs are also expensive, but I tried to present alternative solutions and free equivalents of presented examples.
Identifiers
There is a wide variety of both programming languages and compilers. Apart from applications created in script languages, we can differentiate applications compiled to the processor's native code. Apart from that, there is a number of methods of protecting applications and their resources, and all of that affects the final result of binary file image on disk.
If we are not sure what the software that we are looking at was created with, as we have no expertise in distinguishing characteristic features in compiled files (section names, imported libraries, etc.), using identification (or detectors), tools that have signature base of popular compilers, program and cryptographic libraries or application security systems, is worth trying. A quick analysis will let us decide what our next step should be (e.g. unpacking the application)
Detect It Easy
DIE detector has a database of most popular security systems, including exe-packers, exe-protectors as well as signatures of popular compilers and linkers. Additionally it has a simple built-in script language, that allows us to add new signature definitions quickly. A PE executable file structure viewer is also available.

| Website | https://horsicq.github.io |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Detect It Easy
DIE detector has a database of most popular security systems, including exe-packers, exe-protectors as well as signatures of popular compilers and linkers. Additionally it has a simple built-in script language, that allows us to add new signature definitions quickly. A PE executable file structure viewer is also available.

| Website | https://horsicq.github.io |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Exeinfo PE
Detector for a whole bunch of executables, exe-packers, archive detector and all sorts of file formats for different operating systems.

| Website | https://github.com/ExeinfoASL |
| Mirror | http://exeinfo.booomhost.com/ |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
ProtectionID
Detector ProtectionID was created to detect games security systems. It has a vast base of signatures from all possible security systems, compilers, and linkers. Even though user interface may not be the best looking, it does the job perfectly and is updated very often.

| Website | http://pid.gamecopyworld.com |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
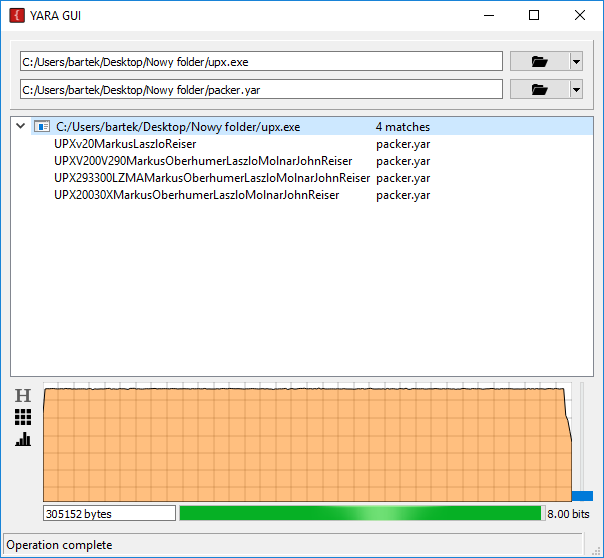
YARA GUI
YARA GUI is a Windows UI frontend for the popular binary pattern matching library and format called YARA.
| Website | |
| Sources | |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| YARA signatures |
|
Disassemblers and decompilers
With knowledge about what we are dealing with or, to be precise, what programming language and compiler this application was created with, we begin analysis in disassembler or decompiler. It is their task to analyze compiled, binary file and display its code and structure in a way easy for a human to understand.
Thanks to the process of disassembling and decompiling we will know all the functions of the application, what text strings are inside and what fragments of code references to them, what outside functions of the operating system are used by the application or which functions are exported (e.g. in the case of DLL dynamic libraries).
Disassemblers job is to depict application's code in the for of low-level assembler, so if analyzed software was written in C++, Delphi, Visual Basic or any other high-level language compiled to native code, the disassembler will show us its object code in the form of x86 or x64 assembler code.
Decompilers are able or try really hard to recreate original high level code from the code of compiled applications. As you can guess, recreating a high level language code, e.g. C++ with recognition of data structures, types and construction of programming language from compiled code of assembler is a very complicated process, so the amount of tools that allow such action is very small and if they are good, they are in the same time very expensive.
Decompilers can be divided basing on categories of software that they are able to analyze. Compilers of languages like e.g. C# (.NET Framework family), Visual Basic, Java generate object code in the intermediate form, meaning that this code is not directly executed by processor like x86 code, it is a pseudo code (so called P-Code), that is executed by a virtual machine of those programming systems (to run we need e.g. .NET Framework or JVM installed).
Such output code, because of its simplicity and most information stored in the form of pseudo instructions and metadata, resulted in the fact that decompiling in such cases is much more simple than decompiling x86 or x64 code. This caused creation of many dedicated decompilers, that became a nightmare of programmers writing in those languages, as it was very easy for anyone to take a peek at unprotected software, practically it's the version with source code wide open.
That was short introduction, now it is time for a list of most popular disassemblers and decompilers and their usage examples.
IDA and Hex-Rays
IDA that is Interactive DisAssembler in an undpisupted king among tools used in reverse engineering. IDA is a disassembler and debugger with built-in code analysis for over 60 types of processors. It has its own script language, large base of signatures of the most popular programming libraries as well as support for plug-ins that additionally enhance functionality e.g. by support for Python scripts.
The most known and valued plugin for IDA is Hex-Rays decompiler, that supports decompilation of x86, x64 and ARM codes, which is invaluable analysis tool.
IDA also has built-in debuggers for many hardware platforms, which makes this a perfect multitool for analysis of various executable files.
| Website | https://hex-rays.com |
| Licence | Commercial from 449 EUR and free demo version. |
| Advantages |
|
| Disadvantages |
|
| Plugins |
|
Ghidra new
Ghidra is a new and free tool directly from the US intelligence agency NSA for the disassembly and decompilation of binary applications.
One of the most outstanding features of Ghidra is the built-in decompiler, which in some cases, such as ARM code analysis, can handle code reconstruction much better than the HexRays decompiler.

It may not be entirely up to the functionality of HexRays at the moment (remember that Ghidra is a new project), but tools such as decompilers require a lot of work and it is rare to see a new product that someone offers for free.
| Website | https://ghidra-sre.org/ |
| License | Apache License 2.0 |
| Advantages |
|
| Disadvantages |
|
| Plugins |
.NET Reflector
When you must face analysis of software created in a programming language based on .NET Framework, e.g. C# or VB#, .NET Reflector decompiler will prove invaluable help. With its help, you will be able to quickly and efficiently take a peek at application's structure and code.
Reflector's big advantage is the fact that it has a small but very useful plugin base, with available, for example a plugin that allows recreating of the whole project for Visual Studio, from decompiled application. In addition, integration with Microsoft Visual Studio allows for simultaneous debugging of own code and code of closed libraries.
Because of simplicity of decompiling programs created for .NET Framework, many security tools were created, of course we are talking here about obfuscators that remove meta data from compiled programs, are able to modify IL code, encrypt text strings etc. If we come across such a program, we should familiarize ourselves with de4dot deobfuscator, that is able to automatically remove protections used by dozens of obfuscator types.
| Website | https://www.red-gate.com/products/dotnet-development/reflector/ |
| Licence | Commercial from 99 USD and free limited time trial |
| Advantages |
|
| Disadvantages |
|
| Plugins |
|
dnSpy abandoned
A real workhorse for .NET decompilation, with built-in IL code editor and debugger. Above all of that, it's free with intuitive and modern interface design.

| Website | https://github.com/dnSpy/dnSpy |
| Licence | GNU GPL v3 |
| Advantages |
|
| Disadvantages |
|
dnSpyEx new
Reincarnation of the excellent dnSpy described above, made by a Polish guy ElektroKill. Updated libraries to support latest .NET versions, fixed bugs. Just download and test.
| Website | https://github.com/dnSpyEx/dnSpy |
| Licence | GNU GPL v3 |
| Advantages |
|
| Disadvantages |
|
JEB Decompiler new
JEBDEC decompiler for Android Dalvik, Intel x86, ARM, MIPS, RISC-V, S7 PLC, Java, WebAssembly and Ethereum platforms.
JEB has filled a gap that IDA lacked, mainly by supporting the decompilation of Android apps. It does this so perfectly that it is now the standard for analyzing these apps.
One of the best reverse engineering tools with built-in deobfuscation of many strategies used by obfuscators not only on Android. Deobfuscation topics with technical details are often covered on their excellent technical blog and it's a real vein of gold for people who are interested in modifying, protecting and deobfuscating mutated code.

| Website | https://www.pnfsoftware.com |
| Excellent technical blog | https://www.pnfsoftware.com/blog/ |
| License | Commercial and a free community edition |
| Advantages |
|
| Disadvantages |
|
Java Decompiler
JD-GUI or Java Decompiler is a decompiler for Java applications, hence its name. It allows for viewing of compiled units code*.class or whole *.jar bundles.
It contains very useful search engine with filters that allow for searching by names, types, constructors, fields, methods and text strings.
Apart from stand alone application there are also plugins for programming environment Eclipse and IntelliJ IDEA, that allow for viewing code of compiled modules.
If you've ever used or you keep using well-known decompiler JAD (that was discontinued in 2001) then it's about time for an update, not only does JD-GUI support new elements of Java language, but also navigation over decompiled project is very easy and fun.
It also needs to be mentioned that, just like with .NET applications, that have been protected with obfuscators, Java applications can be protected and then decompiler functioning is limited or even impossible.

| Website | http://java-decompiler.github.io |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
JustDecompile
Free alternative for commercial.NET Reflector developed by Telerik known for UI components. Free doesn't mean worse, it has built-in reference search engine, generating projects from decompiled sources ability as well as support for plugins, including de4dot deobfuscator plugin.

| Website | https://www.telerik.com/products/decompiler.aspx |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
ReFox
Decompiler for applications created with database programming environment Visual FoxPro from Microsoft. This is a very niche solution for equally niche environment, but there are no alternative solutions that would allow for analysis of those application and those that do exist have been discontinued and don't support latest versions of VFP applications. ReFox allows for decompiling of classes, viewing forms and built-in data.

| Website | |
| Licence | Commercial from 290 EUR and demo version. |
| Advantages |
|
| Disadvantages |
|
VB Decompiler
Applications created with Visual Basic 5 and 6 are all in the past now. However, internal structure of code based on P-Code was a cradle for .NET technology and from the very beginning it's been causing problems with code analyze, as there were no dedicated tool for its analyze. We can say that VB Decompiler was created a bit too late for the market's needs, but is irreplaceable when analyzing Visual Basic applications (EXE, DLL as well as OCX controls) compiled to P-Code (Visual Basic also allowed from compiling to x86 code).
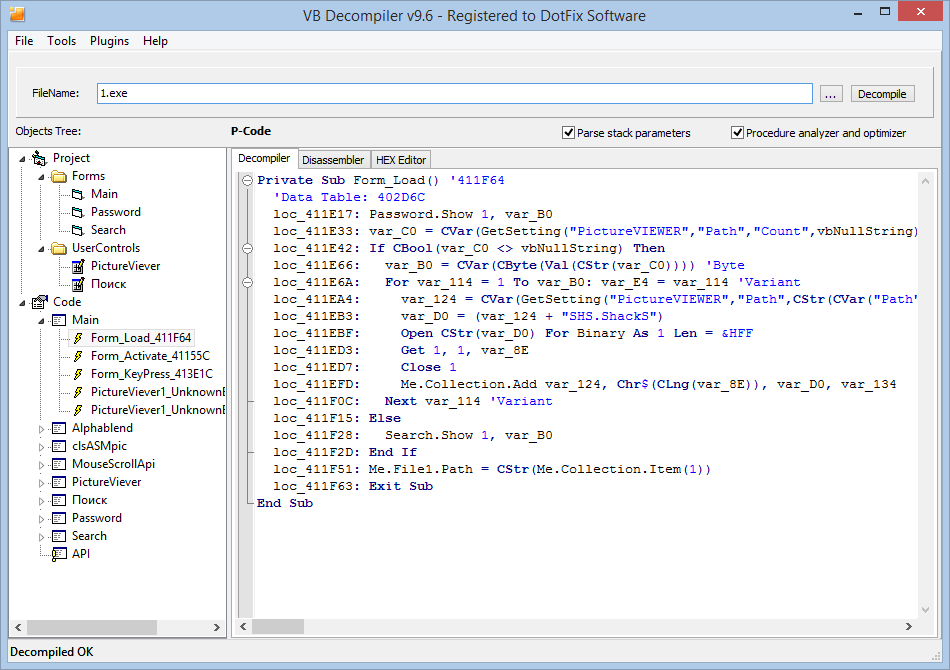
| Website | https://www.vb-decompiler.org |
| Licence | Commercial from 99 EUR, as well as lite version. |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
IDR
Disassembler and decompiler IDR or Interactive Delphi Reconstructor is a tool meant only for application analysis in popular Delphi environment. It is a very useful tool comparing to e.g. IDA because it can analyze internal structures of Delphi application, has built-in form viewer, that allows for fast and easy finding of events assigned to controls on the form (e.g. button1.OnClick). IDR has vast databases of signatures of standard Delphi environment libraries in all available versions, so in output deadlisting we will see friendly function names.
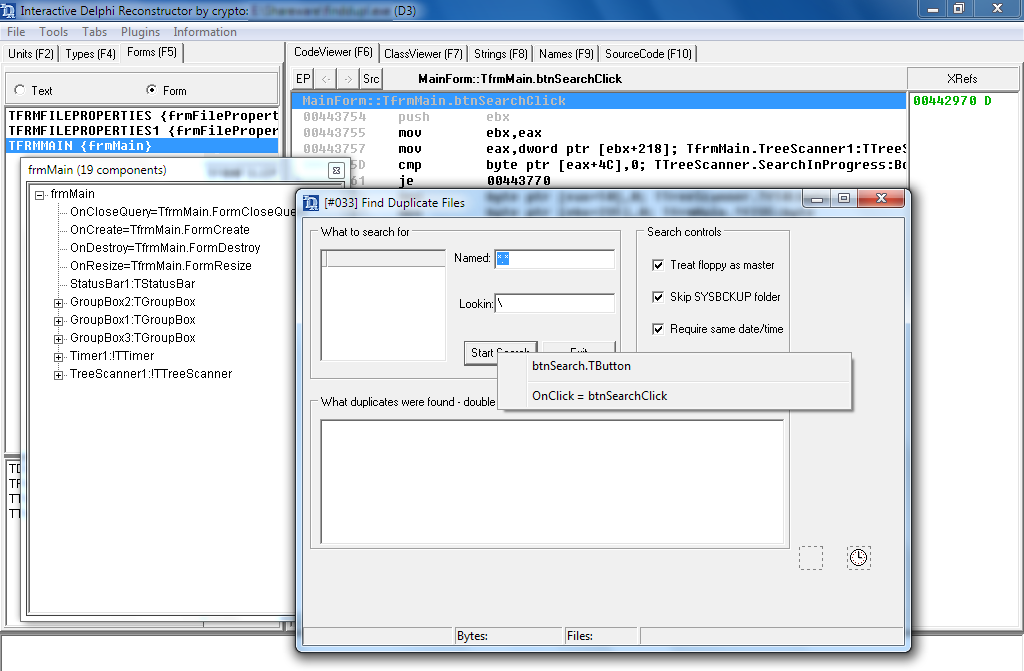
| Website | http://kpnc.org/idr32/en/ |
| Licence | Freeware with optional paid current copy (unknown terms and conditions, author couldn't be contacted). |
| Advantages |
|
| Disadvantages |
|
Debuggers
Every programmer sooner or later gets to know the functioning of a debugger in his favourite programming environment. Thanks to debugger we are able to track application running in real time, see how instructions affect contents of memory or variables and detect potential errors. However debugging of our own software, when we have access to information about source code and usually debug high-level code, straight from programming environment, is a piece of cake compared to debugging of application without access to source code. This is where dedicated debuggers, with advanced analysis of binary application structures, come in handy, but their use requires knowledge of low-level languages as well as basis of functioning of processor, for which this application was compiled.
OllyDbg
This is de facto a standard debugger for Windows in the world of reverse engineering (alongside built-in debugger for IDA disassembler). It has capabilities of application code analysis and allows for interference with almost every aspect of application running.
Other interesting functions include OllyDbg that allows for conditional code tracing, has vast plugins database, including those hiding its presence from anti-debug methods (Phant0m plugin), or plugins that allow for controlling of debugger running from the script level (ODbgScript plugin), while those scripts, most often used for unpacking of unprotected applications, come in hundreds.
Popularity of OllyDbg is obvious with the fact, that no other debugger, including legendary SoftICE system debugger has had so many plugins and modified versions like OllyDbg. It is interesting that a special version OllyDbg was created under the name of Immunity Debugger with built-in Python script support, meant for analyzing malware and creating exploits
There are currently two versions of OllyDbg, old with number 1.10, that has the most extensions and new version 2.01 that is becoming more and more popular. It is good news that a new 64-bit version is being developed because of the popularity of 64-bit operating systems.


| Website | http://www.ollydbg.de |
| Licence | Shareware for free, according to website (upcoming freeware?) |
| Advantages |
|
| Disadvantages |
|
| Plugins |
|
| Alternatives |
|
x64dbg new
x64dbg are basically two debuggers, one dedicated for 64 bit software debugging and second for 32 bit applications. It features modern interface, plenty of configuration options, internal engine based on modern programming libraries like TitanEngine, Capstone Engine, Keystone Engine.
Number of supported features is really impressing, plugins, built-in scripting language, Yara signatures scanning, built-in decompiler and many more. And it's development is very active. Taking the fact that 64 bit OllyDbg never left the development stage, x64dbg has become de facto standard debugger for 64 bit applications.

| Website | https://x64dbg.com |
| Sources | https://github.com/x64dbg/x64dbg |
| License | GNU GPL v3 |
| Advantages |
|
| Disadvantages |
|
| Plugins |
|
| Alternatives |
|
DILE
Debugger for .NET Framework applications. It is quite a robust tool, but sometimes invaluable. It looks a bit like Visual Studio built-in debugger, I'm mentioning it only because it is one of very few debuggers for .NET applications without access to source codes, there are also plugins for .NET Reflector for the purpose of debugging (Deblector plugin).
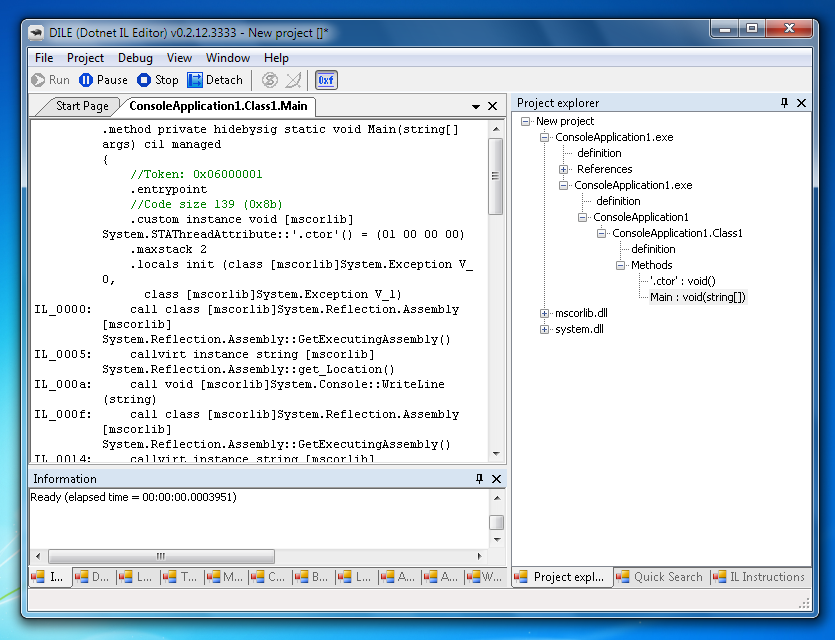
| Website | https://sourceforge.net/projects/dile/ |
| Licence | GNU GPL |
| Advantages |
|
| Disadvantages |
|
Hex editors
If you have analyzed your application in disassembler, traced its running in debugger, there may be a need to interfere with program code in order to input corrections or to change some text strings, fix values or other information included in application's binary file.
For that purpose hex editors are used. At times when I used to read games magazine Top Secret, I associated hex editors only with save games modification, as readers were sending numerous offsets (addresses in a file) as well as values that needed to be changed in save files, e.g. to get a certain amount of cash or other resources in the game.
There are many hex editors on the market, with numerous different functions and applications, like e.g. built-in view over data structure (meaning that this hex editor can visually display for example bitmap elements or internal structure of exe file). An example of such an editor is e.g. well known WinHex, that is used in data retrieval (it contains built-in support for many system files), however, in my opinion, it is not very good for works connected with 'digging' in application's binary files, despite the fact that it has appropriate functions.
HIEW
This is my number one for hex editors, I cannot imagine my work without it. It is seemingly an old console application, but in reality it is a true beast. HIEW (by Hacker’s View) is a hexeditor, disassembler that supports architecture of x86, x64, ARM V6 processors, it also supports NE, LE, PE/PE32+, ELF/ELF64 files. This program has vast user database has been developed since 1991 and updates are regular.
Thanks to HIEW, we are able not only to edit binary file data but if that is an application, also its code. Built-in disassembler allows for navigation over the code and its functions as well as to easily modify existing instructions with the help of built-in assembler, which means that you don't have to know hex codes by heart. Instead, it is enough to write e.g. mov eax,edx and HIEW will automatically compile that instruction and insert it into binary file.
HIEW is also able to repeatedly replace tools like IDA, if we have a simple task to do, its greatest advantages are its ability to operate very fast and built-in code analysis and direct modification options.

| Website | https://www.hiew.ru |
| Mirror | https://www.hiew.io |
| Licence | Commercial from 19 USD and demo version. |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Hex Workshop
Windows hex editor with many useful options, file comparison, bit operations on code blocks, generating checksums, contains structure view for the most popular types of files.

| Website | http://www.bpsoft.com |
| Licence | Commercial from 89.95 USD and time-limited version. |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
HxD
Free hex editor with basic functions and options like edition, search, file comparison. It allows for simultaneous work with multiple files. It is also possible to open memory of different processes and gain direct access to discs.
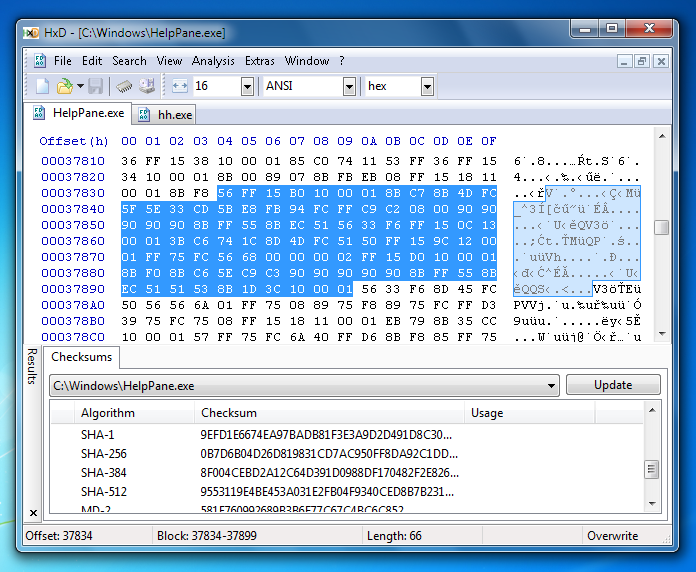
| Website | https://mh-nexus.de/en/hxd/ |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Resource editors
Characteristic feature of Windows applications is the fact all resources like icons, images, forms, localized texts, as well as other information, can be saved in PE file structure, within a special area called resources. Those data are saved when linking. As all application files are saved in one EXE or DLL output file, if there is a need to change those information and if their size is unchanged, we will be able to modify them using hex editor, however, if we need to add new data or set different that have a larger size (e.g. longer text or another image), because of the structure of those data we will have to use proper resource editor.
Apart from modifications in application's resources, resource editors are also used just for taking a peek what additional data are stored in the application's file.
Resource Hacker FX
Resource Hacker used to be one of the most popular resource editors, but it has been discontinued for a long time, despite that fact of its popularity, new patches have been created that gave this editor a new life.

| Website | https://ramensoftware.com/resource-hacker-fx |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Resource Tuner
Excellent resource editor from the creators of PE Explorer. It contains built-in unpackers, e.g. for UPX or FSG compressor, resource edition can be also done with use of friendly wizards. Resource Tuner has also built-in scanner that allows for scanning of any given catalogue for resources of a specific type.
| Website | http://www.heaventools.com/resource-tuner.htm |
| Licence | Commercial from 49.95 USD and 30 days trial version. |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Editors and support tools
Reverse engineering requires specialized tools for specific purposes, other than standard ones like disassemblers, decompilers and debuggers – there are many dedicated tools that help in analysis of applications as well as editors, some of them you will find below.
PE-Bear
Excellent browser and file structure editor, with built-in simple disassembler, PE file compare basing on values from all structures (solution that is unique on a world scale), detection of popular exe-packers / exe-protectors, hex editor and graphic visualization of section structure.
Tool created by a Polish programmer (yes, you got it right) is perfect for low-level analysis of PE/PE32+ files, created mostly for the purpose of malware analysis.
| Website | https://hshrzd.wordpress.com/pe-bear/ |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
PeStudio
An interesting tool that apart from displaying basic information about exe file, has also a set of rules that can detect incorrect elements in the structure of exe file (all sorts of anomalies) as well as elements that can potentially indicate that the file has been infected. Very useful tool for those who work with PE files every day.
| Website | https://www.winitor.com |
| Licence | Free for non-commercial use. |
| Advantages |
|
| Disadvantages |
|
PEAnatomist new
A browser of internal PE file structures, supporting such formats as PE32, PE32+, COFF and the various processor architectures for which PE images have been created.
| Website | https://rammerlabs.alidml.ru/peanatomist-eng.html |
| License | Freeware |
| Advantages |
|
| Disadvantages |
|
Recaf new
Recaf is an open-source Java bytecode editor that simplifies the process of editing compiled Java applications. To make things easier Recaf abstracts away much of the internal class file format. Difficult tasks such as updating stack-frames are done automatically. Along with additional features to assist in the process of editing classes, Recaf is the most feature-rich free bytecode editor available.
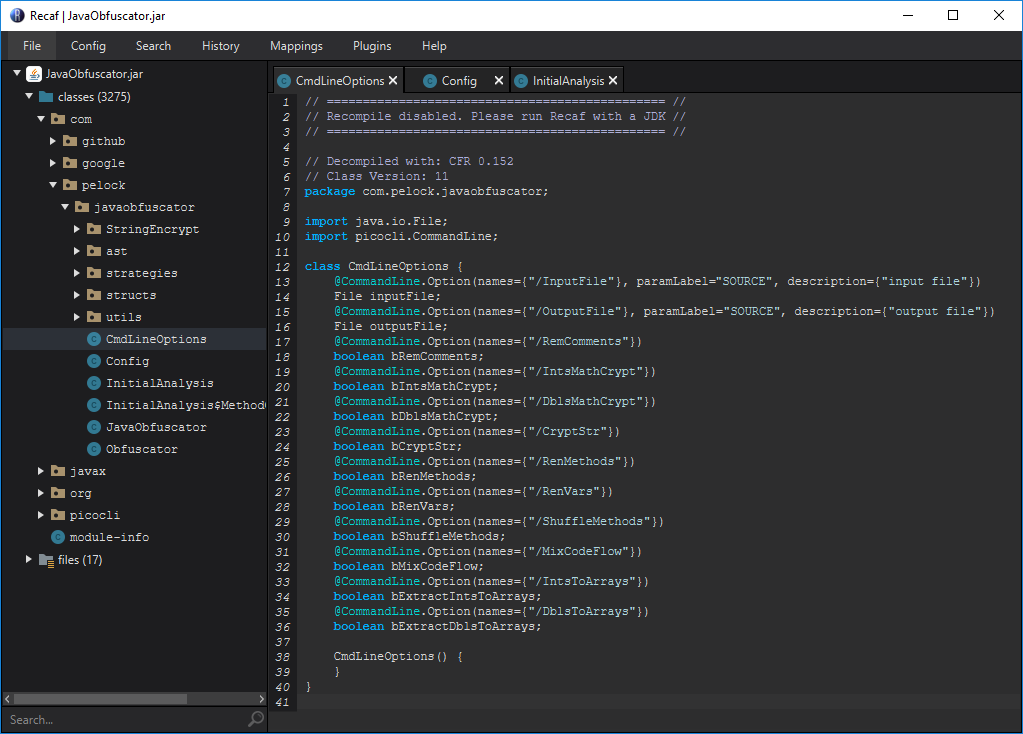
| Website | https://www.coley.software/Recaf/ |
| Sources | https://github.com/Col-E/Recaf |
| Licence | MIT |
| Advantages |
|
| Disadvantages |
|
dirtyJOE
Advanced editor for compiled Java files. Unique tool, developed by Polish author, for code modifying, with built-in disassembler and assembler, this editor allows also for modifying all structures within compiled *.class files. dirtyJOE is useful when we want to modify protected files (after using obfuscator for Java), when traditional methods of decompilation, modification and recompilation fail, dirtyJOE proves irreplaceable.
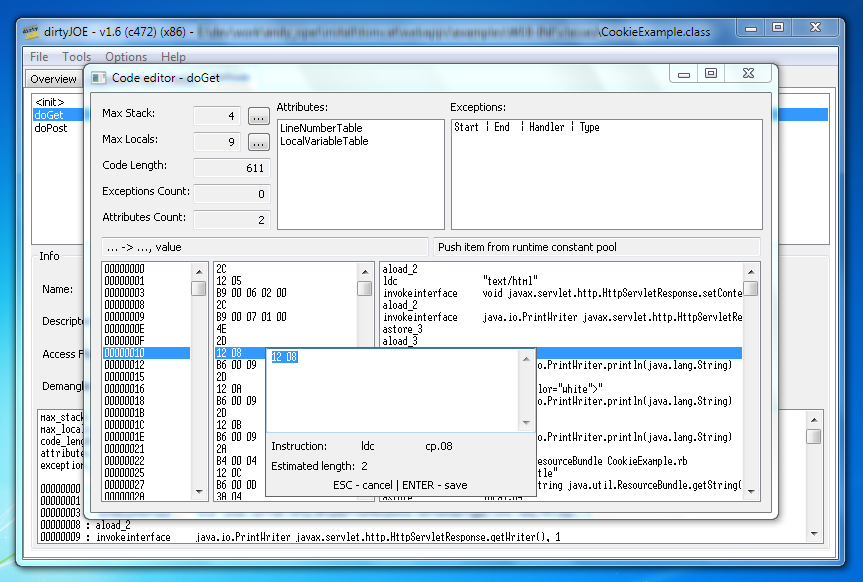
| Website | http://dirty-joe.com |
| Licence | Free for non-commercial use. |
| Advantages |
|
| Disadvantages |
|
Extractors and rippers
Application files, just like application bundles, can contain additional information, like e.g. hidden icons, sound files, libraries, etc. If we want to have a quick check of what's inside the application or e.g. inside the whole installation package of software, we must use appropriate extractor or ripper.
Universal Extractor
This software allows for the extraction of files from archives, self unpacking archives, and installers. This is very useful when we want to learn what's inside the installer package, where often we can find some additional installation scripts or auxiliary libraries, without actually running the installation process.
| Website | https://www.legroom.net/software/uniextract |
| Licence | Freeware |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
MultiExtractor
Extractor of all kinds of multimedia files, like graphic files, icons, sound files, movies, 3D models, Flash animations. Dynamic data unpacking from processes memory and simple viewer make this software a very interesting tool, when we want to take a quick peek what's inside application files.

| Website | https://www.multiextractor.com |
| Licence | Commercial from 19 USD and demo version. |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Virtual environments
Analysis of unknown software can be risky, especially when we have to run the software and just doing this with debugger can end up badly if the software runs a thread in the background which can install a rootkit or other malware. It is a good idea to be protected against such accidents and run suspicious software under the supervision of a virtual machine.
VMware
The most famed software that creates a virtual environment, where we can install any operating system and test software without unnecessary risk.

| Website | https://www.vmware.com/products/workstation-pro.html |
| Licence | Commercial from 225 EUR and free trial version. |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Sandboxie abandoned
This software creates virtual sandbox for applications that are run. All operations within virtual sandbox are isolated and have no influence over the system. This is a perfect solution for debugging or quick test of correctness of application's running without fear for side effects.
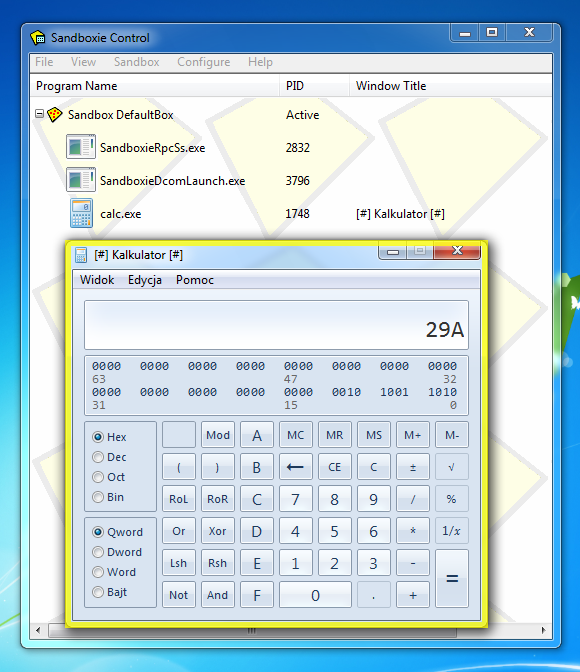
| Website | https://www.sandboxie.com |
| Licence | Commercial from 15 EUR and free trial version. |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
Sandboxie Plus & Classic new
Sandboxie is a sandbox-based isolation software for 32 and 64-bit Windows NT-based operating systems. It is being developed by David Xanatos since it became open source, before that it was developed by Sophos (which acquired it from Invincea, which acquired it earlier from the original author Ronen Tzur). It creates a sandbox-like isolated operating environment in which applications can be run or installed without permanently modifying the local or mapped drive. An isolated virtual environment allows controlled testing of untrusted programs and web surfing.
| Website | https://sandboxie-plus.com/ |
| Sources | https://github.com/sandboxie-plus/Sandboxie |
| Licence | GPL 3.0 |
| Advantages |
|
| Disadvantages |
|
| Alternatives |
|
This is not the end, this is just the beginning...
Presented tools are just a part of what can be found on the market. There many other free or experimental projects as well as those that were abandoned at some point but are still worth a look. I encourage you to discover secrets of reverse engineering and if you should find something interesting - write me an email.