PELock Software Protection & Software License Key System
Software copy protection against cracking & reverse engineering with anti-cracking & anti-debugging techniques. Software license key system with time trial options.
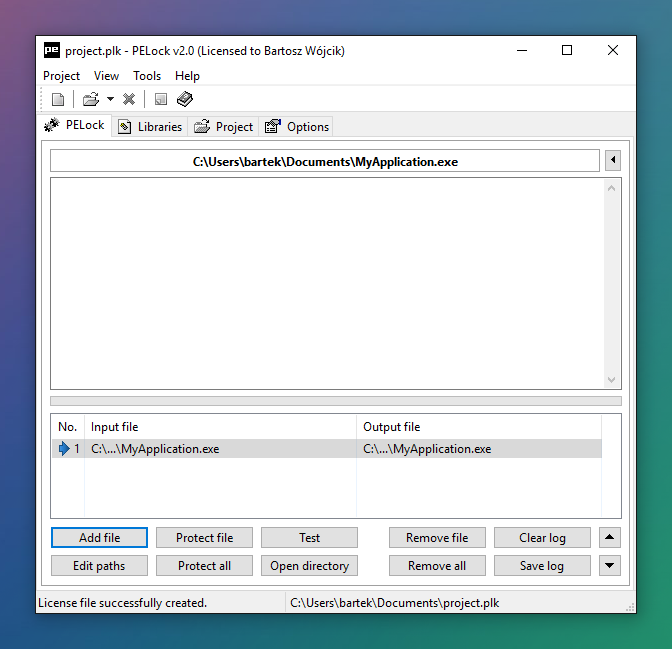
Software protection system
PELock is a software security solution designed for the protection of any 32 bit Windows applications against cracking, tampering and reverse engineering analysis.
PELock comes with a built-in licensing system, which you can use to easily add a license key system to your application. You can also set various time-trial limitations for the protected application, e.g. 30 day trial.
You can closely integrate the protection and licensing features into your application using the dedicated SDK. The SDK comes with hundreds of examples for C/C++, Delphi, Lazarus, Freepascal, PureBasic, PowerBASIC, D, and Assembler with full source code.
You can protect any compiled application file for Windows as long as it's compatible with the Portable Executable format, no matter what programming language or development environment was used to create it.
| Supported file formats | Extensions | |
|---|---|---|
| Applications | EXE | |
| Screensavers | SCR | |
| Dynamic Link Libraries | DLL | |
| ActiveX controls | OCX | |
| Control Panel extensions | CPL | |
| Borland library packages | BPL DPL | |
| Audio codecs | ACM | |
| DirectShow filters | AX | |
Why protect software?
Software piracy
It does not usually take long after an application is released before illegal serial numbers, cracks, patches or key generators (keygens) can be found online for the application.
Usually the reason behind this is weak registration schemes, but even the most sophisticated license key verification algorithms like digital signatures or strong cryptography aren't a problem for crackers if the application file is not protected against modifications and patching of its compiled code.
| Protections | Weak points | Attack vectors |
|---|---|---|
|
key generator keygen crack | |
|
key generator patch crack | |
|
emulator patch crack | |
|
loader patch crack | |
|
unpacker inline patch debug loader | |
|
proxy patch crack |
Can you say that your software is protected in all aspects? PELock gives you solutions for all of the above threats, so you don't have to design, implement and test your own software protection using your customers' systems as a testing ground for your non-standard methods.
Intellectual property theft
Unprotected software is highly vulnerable to reverse engineering analysis, and by using specialized reverse engineering tools it's possible to gather a lot of information from a compiled application. It's possible to recover fragments of original source code, e.g. secret algorithms, and in certain conditions it's even possible to restore the entire source code of the application.
Competitors can take advantage of the technical knowledge obtained in the process of reverse engineering to clone functionality of your software. These are not things taken from movies about hackers but harsh realities that can affect any software maker.
Game hacks
Computer games are exposed to hacks — applications that can modify a game's internal code and algorithms to give an unfair advantage over other players in online battles and tournaments.
An example of a game hack is a popular modification for FPS games called a wallhack. It allows you to see other players' positions through the walls. Another popular modification is called aimbot, an automated bot that can perfectly aim your gun at your opponents and fire.
Proliferation of game hacks can kill the popularity of a game, since the game is ruined for honest players.
Conclusions
Losses to software developers due to cracking and reverse engineering can be huge, for both large and small companies, and it can hurt even more if you are an independent software developer, so you should always consider the appropriate software protection during the software design process.
In-house protections are not always really secure and safe. It pays to use a time-tested solution such as PELock, which uses the latest technical achievements in the field of software protection, and at the same time guaranteeing the maximum level of compatibility and stability.
What is required to protect an application?
To protect your software with PELock, all you need is the compiled application file. If you have access to the source code it's highly recommended to use PELock SDK system functions to introduce additional protections and to use license key system functions.
SDK & usage examples
The SDK provides dedicated macros and functions which are responsible for communication between the protected application and the protection layer.
The more SDK features you will use, the better the protection and application integration will be, and so cracking or reverse-engineering the application will be more difficult for the attacker. The SDK and its usage examples are available in many programming languages e.g.:

C & C++
Are you programming in C or C++? PELock has hundreds of usage examples, and SDKs compatible with many popular compilers and programming environments including Visual C++, Intel C++ Compiler, GCC, MinGW, G++, Clang, C++Builder, Watcom C++, LCC, Pelles C, Digital Mars.

Delphi & Pascal
If you're building software in Delphi, no matter the version, you will find many usage examples and an additional component that makes PELock SDK usage even easier. You can also find usage examples for the Lazarus IDE and FreePascal compiler.

PureBasic
PureBasic is a modern version of the BASIC language with excellent code optimization, many built-in language functions and a devoted fan base. PELock fully supports this programming language and provides a dedicated SDK with hundreds of usage examples.

PowerBASIC
PowerBASIC is an another version of the BASIC language, dedicated to building GUI and console Windows applications with a huge developer community. PELock fully supports this programming language and provides a dedicated SDK with hundreds of usage examples.
What does the protection process look like?
The protection process is fully automated (it can be run from the command line) and consists of rebuilding, modification and encryption of the compiled software, its code, data structures, and adding additional code which manages the protection.
Application and protection code integration example
Below you can find sample usage of the basic encryption macros from the licensing system. Code between the two markers is encrypted during the protection process, and after the application is launched, the code is decrypted and executed only if a valid license key is found. The license key contains the decryption keys, so decryption is impossible without it. After the code is executed it gets re-encrypted.
- C / C++
- Delphi / Pascal
- D
- PowerBASIC
- PureBasic
#include <windows.h>
#include <stdio.h>
#include <conio.h>
#include "pelock.h"
int main(int argc, char *argv[])
{
// code between DEMO_START and DEMO_END will be encrypted in the
// protected file and will not be available without the license key
DEMO_START
printf("Hello world from the full version of my software!");
DEMO_END
printf("\n\nPress any key to exit . . .");
getch();
return 0;
}procedure TfrmMain.FormShow(Sender: TObject);
begin
{$I DEMO_START.INC}
lblInfo.Caption := 'Hello world from registered version';
{$I DEMO_END.INC}
end;import std.stdio;
import std.string;
import core.stdc.stdio;
import core.sys.windows.windows;
import PELock;
int main(string args[])
{
// code between DEMO_START and DEMO_END will be encrypted in the
// protected file and will not be available without the license key
mixin(DEMO_START);
writef("Hello world from the full version of my software!");
mixin(DEMO_END);
writef("\n\nPress any key to exit . . .");
getchar();
return 0;
}#COMPILE EXE
%USEMACROS = 1
#INCLUDE "win32api.inc"
#INCLUDE "pelock.inc"
FUNCTION PBMAIN () AS LONG
' code between DEMO_START and DEMO_END will be encrypted in the
' protected file and will not be available without the license key
DEMO_START
MSGBOX "Hello world from the full version of my software!"
DEMO_END
END FUNCTIONIncludePath "..\..\..\..\..\SDK\English\PureBasic\"
XIncludeFile "pelock.pb"
; start
; code between DEMO_START and DEMO_END will be encrypted in the
; protected file and will not be available without the license key
DEMO_START
MessageRequester("PELock", "Hello world from the full version of my software!")
DEMO_ENDProtected & unprotected application differences
After protection, the application code is modified to protect it from reverse engineering analysis and attempts to recover its original form, which would make it possible to analyze or modify its code and data. Code, data and additional application resources are encrypted using strong cryptographic algorithms and multilayer polymorphic encryption. The protection code itself is transformed into a highly secure form using innovative metamorphic engine. It makes the analysis of the entire protection an extremely technically difficult and time consuming task, even for reverse engineering professionals.
It's worth mentioning that after the protection, the application code is strictly integrated with the protection code; if an attacker tries to remove the protection code, the application itself will remain safe and it will be impossible to run and use it.
Software licensing
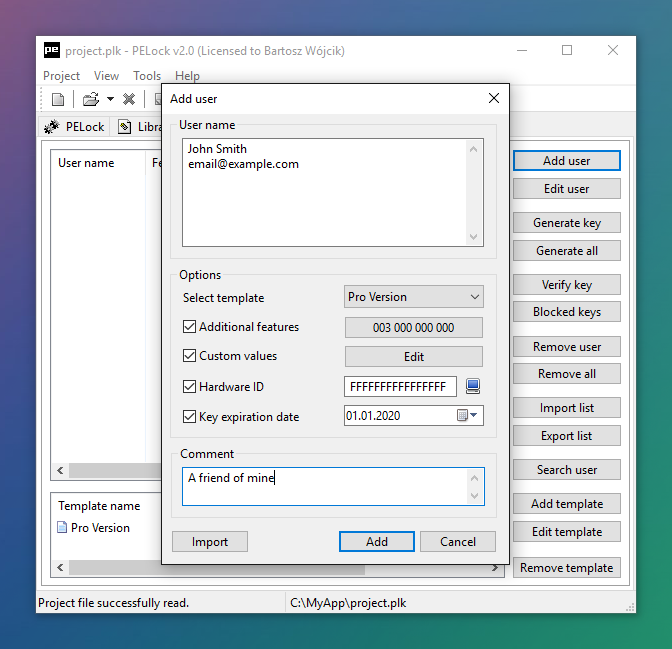
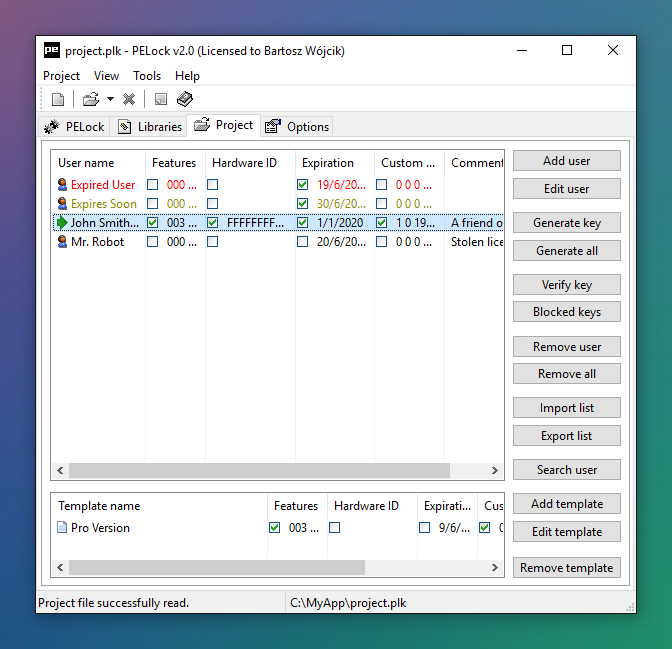
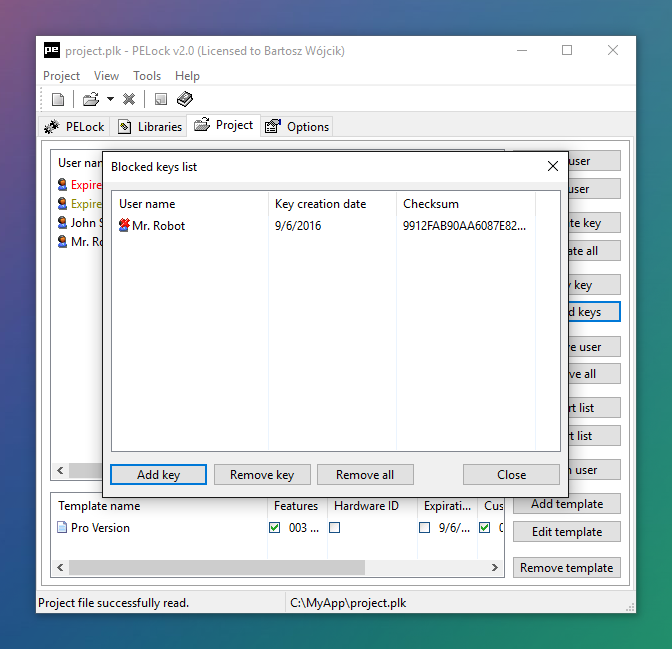
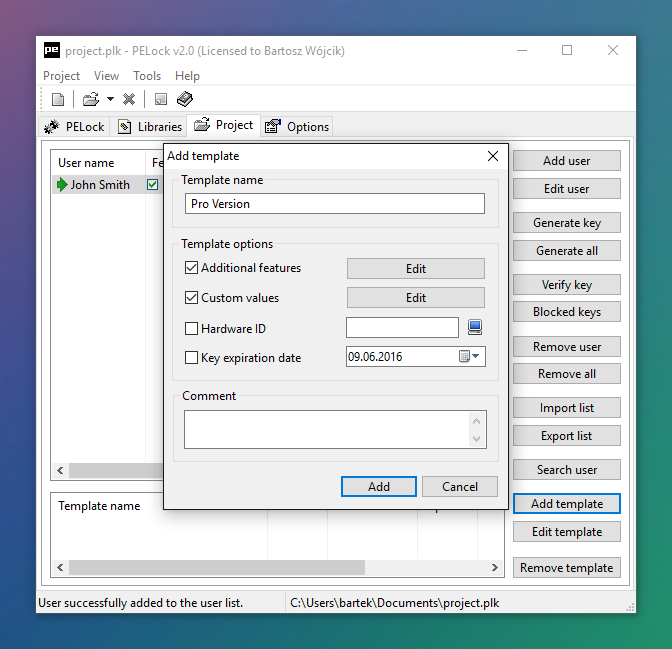
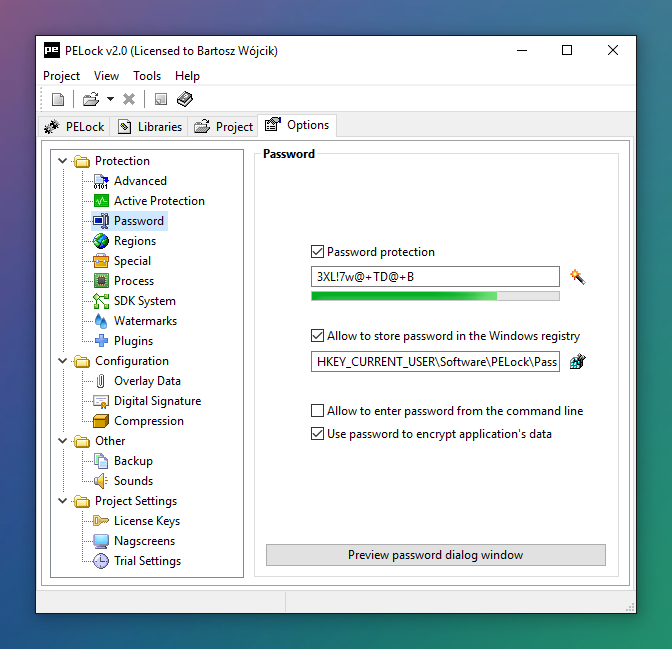
PELock provides a feature-rich license key system. It lets you control your software's features using license key settings.
With its built-in license key manager you can easily add and manage license keys and users for your software, generate and verify license keys, and block illegally shared keys.
The license key system provides many API functions that can be used to read the name of the registered user from the key, verify key validity or read additional integer values and other data saved in the license key.
License key system usage example
Below you will find an example of how to read additional integer values stored in the license key that can be used anyway you want in your software:
- C / C++
- Delphi / Pascal
- D
- PowerBASIC
- PureBasic
#include <windows.h>
#include <stdio.h>
#include <conio.h>
#include "pelock.h"
int main(int argc, char *argv[])
{
unsigned int nNumberOfItems = 0;
// code between DEMO_START and DEMO_END will be encrypted in the
// protected file and will not be available without the license key
DEMO_START
printf("Hello world from the full version of my software!\n");
// read key integer value - you can use it however you want
// you can store up to 16 integer values in license key
nNumberOfItems = GetKeyInteger(5);
printf("You can store up to %u items in the database\n", nNumberOfItems);
DEMO_END
printf("\n\nPress any key to exit . . .");
getch();
return 0;
}
procedure TfrmMain.FormShow(Sender: TObject);
begin
{$I DEMO_START.INC}
lblInfo.Caption := 'Hello world from registered version';
// read integer from the license key (indexes from 1-16)
lblLicenses.Caption := 'License count: ' + IntToStr(GetKeyInteger(1));
{$I DEMO_END.INC}
end;import std.stdio;
import std.string;
import core.stdc.stdio;
import core.sys.windows.windows;
import PELock;
int main(string args[])
{
// initialize PELock class
PELock myPELock = new PELock;
uint nNumberOfItems = 0;
// code between DEMO_START and DEMO_END will be encrypted in the
// protected file and will not be available without the license key
mixin(DEMO_START);
writef("Hello world from the full version of my software!\n");
// read key integer value - you can use it however you want
// you can store up to 16 integer values in license key
nNumberOfItems = myPELock.GetKeyInteger(5);
writef("You can store up to %d items in the database\n", nNumberOfItems);
mixin(DEMO_END);
writef("\n\nPress any key to exit . . .");
getchar();
return 0;
}#COMPILE EXE
%USEMACROS = 1
#INCLUDE "win32api.inc"
#INCLUDE "pelock.inc"
FUNCTION PBMAIN () AS LONG
DIM nNumberOfItems AS LONG
nNumberOfItems = 0
' code between DEMO_START and DEMO_END will be encrypted in the
' protected file and will not be available without the license key
DEMO_START
MSGBOX "Hello world from the full version of my software!"
' read key integer value - you can use it however you want
' you can store up to 16 integer values in license key
nNumberOfItems = GetKeyInteger(5)
MSGBOX "You can store up to " & STR$(nNumberOfItems) & " items in the database"
DEMO_END
END FUNCTIONIncludePath "..\..\..\..\..\SDK\Polish\PureBasic\"
XIncludeFile "pelock.pb"
; start
nNumberOfItems.l = 0
; code between DEMO_START and DEMO_END will be encrypted in the
; protected file and will not be available without the license key
DEMO_START
MessageRequester("PELock", "Hello world from the full version of my software!")
; read key integer value - you can use it however you want
; you can store up to 16 integer values in license key
nNumberOfItems = GetKeyInteger(5)
MessageRequester("PELock", "You can store up to " + Str(nNumberOfItems) + " items in the database")
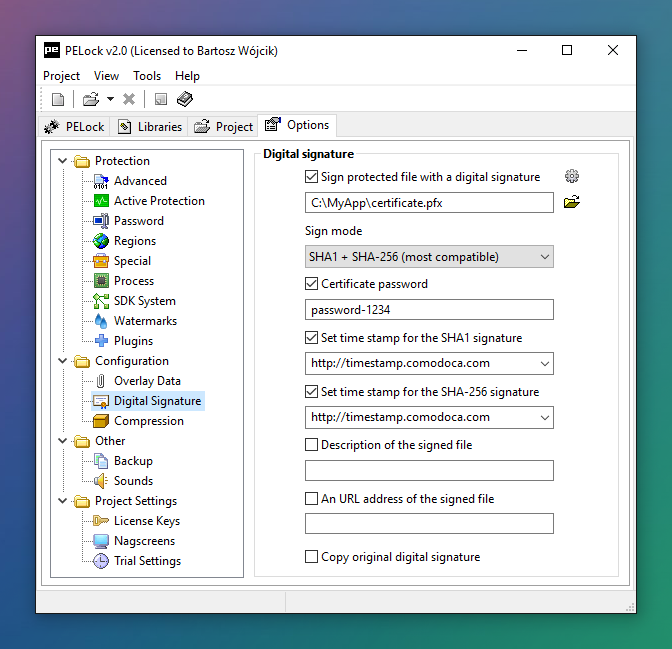
DEMO_ENDLicense keys are generated using strong cryptographic algorithms like RSA-2048. It's impossible to create unauthorized license keys without the PELock project file.
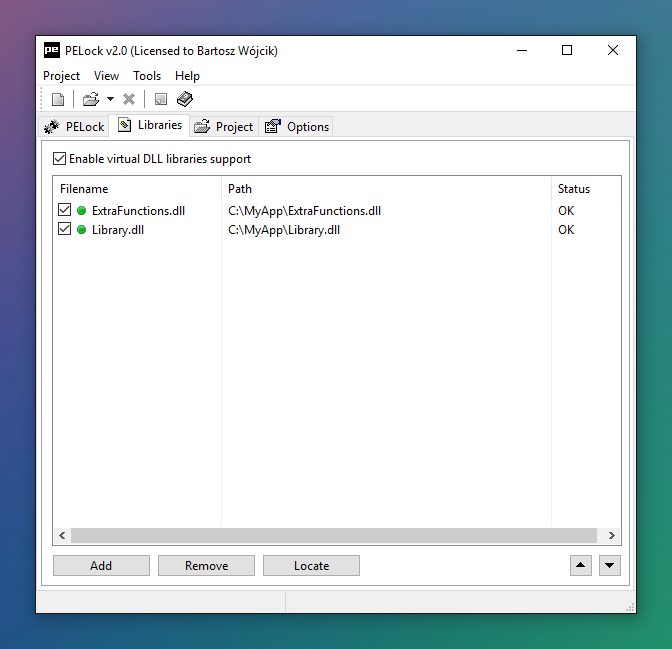
Virtual DLL libraries
PELock has a built-in binder for additional application DLL libraries. It's possible to merge your main application EXE file with any number of extra DLL libraries into a single output EXE file.
If your application uses or requires additional DLL libraries you can hide them inside the protected application; no third party will be able to view it, nor will any other program have access to it, because the whole loading process is emulated in memory and nothing is written to disk, and it's completely transparent from the application's perspective.
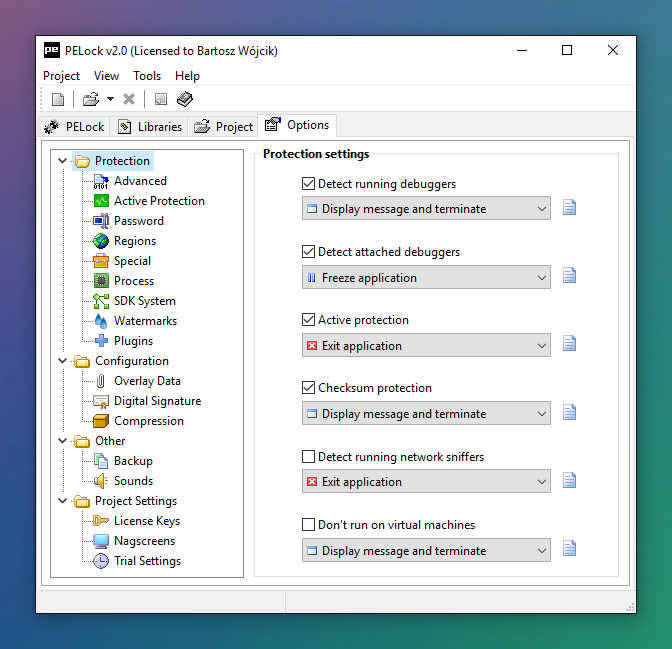
Configuration flexibility
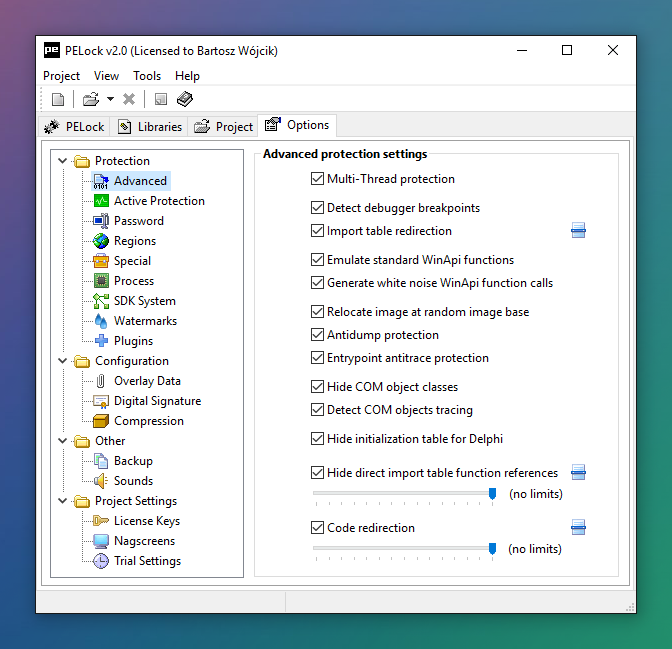
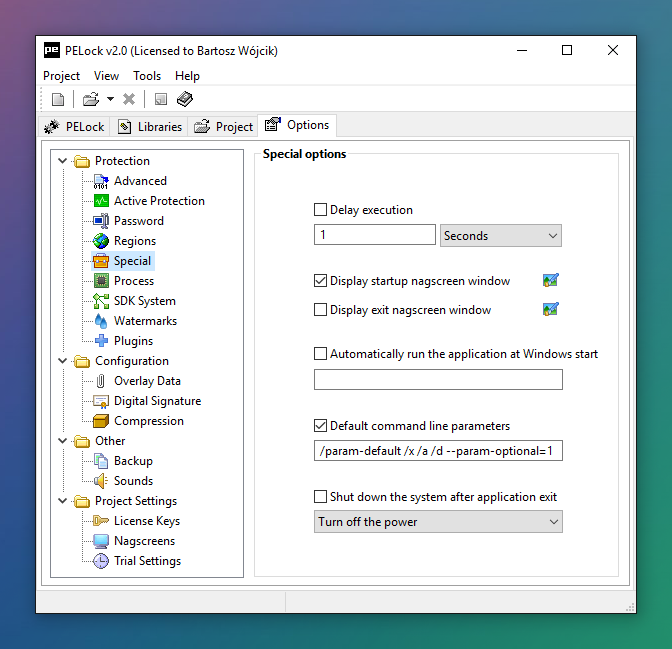
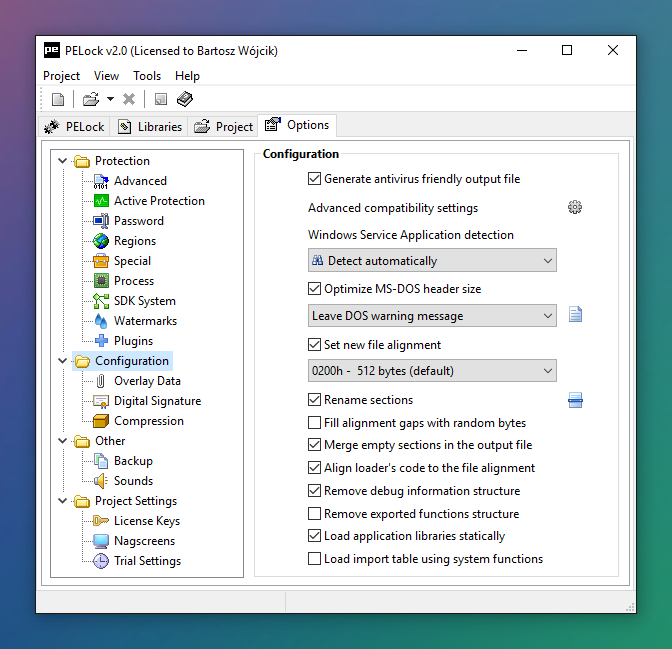
For proper application protection you don't have to change any of the default settings. But if you want, take a look at the Options tab. You'll find a variety of additional configuration settings that allow you to adjust the protection to the smallest detail to suit your needs.
Discover hundreds of extra PELock features, so that you will not need to use any other protection tools for your application.
All options are described in detail in the help file. Do not be afraid to experiment; with just one click you can restore all default settings.
Compatibility & stability
PELock has been tested for all available 32 and 64 bit versions of the Windows operating system. And I'm not talking here only about the latest two or three versions of Windows.
Both PELock and the protection code added to the applications are compatible with:














Guaranteed stability
Making PELock compatible with all Windows versions required thousand hours of work, analysis, testing and bug fixes. Do you know any other software compatible with both the latest and the oldest Windows operating systems? All of them.
Thanks to this enormous effort — PELock guarantees stable operation of your protected software regardless of the conditions in which it will be launched.
Protection against exploits & 0day vulnerabilities
PELock fully supports applications that make use of the latest anti-exploitation mitigation methods built into new Windows versions and integrated with applications using special compiler options. Mitigation features are properly handled and fully functional for the protected applications.
As a result, your application will be protected against cracking, but you will not have to give up the extra security against exploits and 0day vulnerabilities.
| Mitigation technique | Short name | |
|---|---|---|
| Control Flow Guard | CFG | |
| Address Space Layout Randomization | ASLR | |
| Data Execution Prevention | DEP | |
| Safe Exception Handling | SAFESEH | |
Compatibility with antivirus software
Other protection makers won't tell you this, but often those systems are incompatible with antivirus software in some way. In those cases, antivirus programs can incorrectly label protected application as an unknown threat, which is called false-positive detection.
The reason behind this lies in certain detection methods used by antivirus programs, often caused by the additional encryption of protected application files that can lead to trouble with some antivirus software systems.

This problem has been deeply analyzed, tested and solved in PELock, through proper rebuilding of the protected application file, so its code, data and internal structure do not arouse any suspicions within antivirus software.
Questions?
If you would like to ask me about PELock, or something's not clear, mail me. I'll be happy to answer all of your questions.